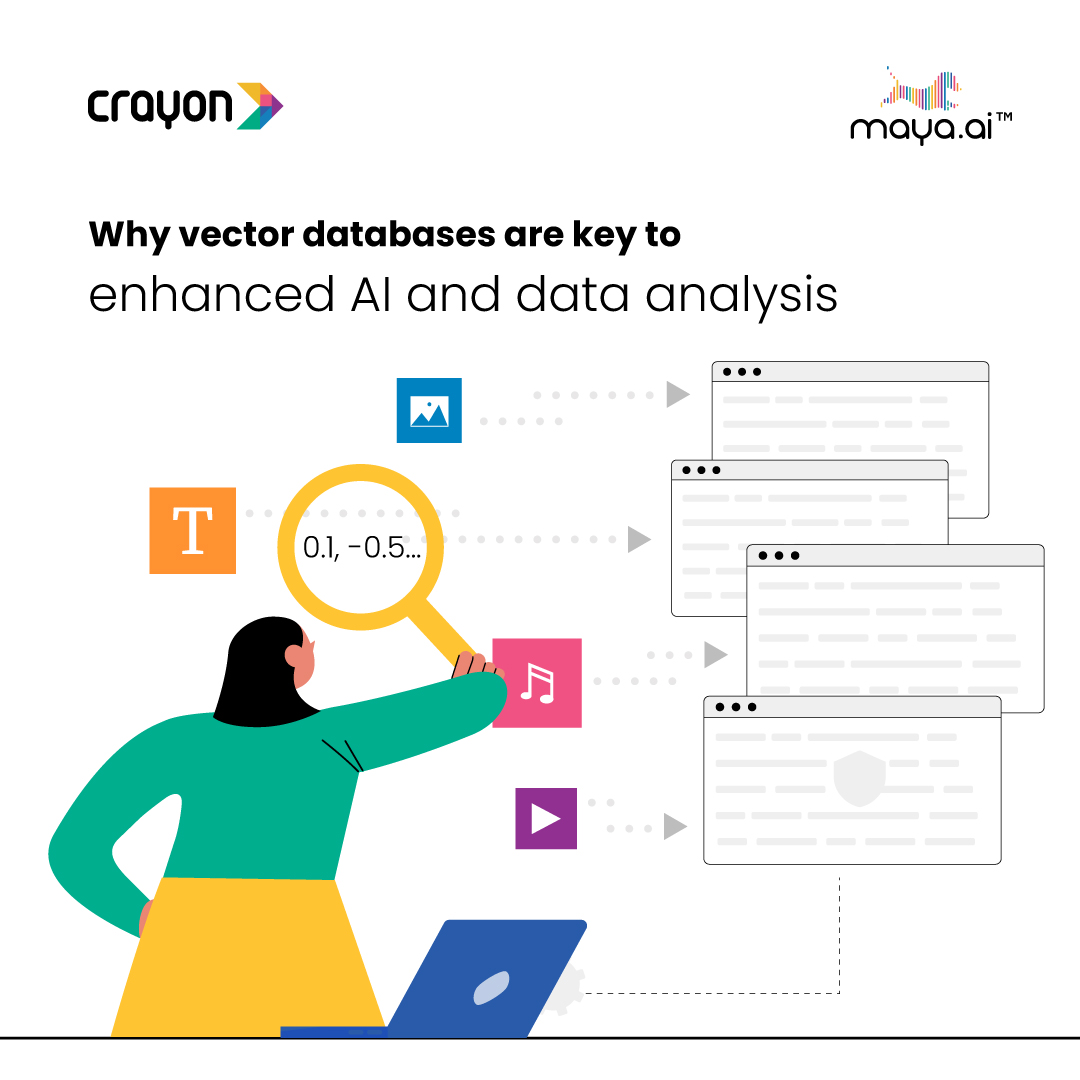
In a data-driven world, it is critical to manage large chunks of data in a simple way. In the words of comedian Dave Chappelle... This is where solutions like vector databases come in. They are significant because of their ability to efficiently store and process...